
Malicious hacks often have an element of opportunism, and any opportunity to steal valuable information is exactly what hackers spend their time searching for.
Even if users keep their own information or system as secure as possible, there are a thousand different servers which might hold personal details that remain for a hacker’s exploit.
From a university server to an international dating website, personal information like addresses, credit card numbers, and email addresses could all be saved here.
When user data gets breached in a large-scale hack or exploit, it puts thousands of identities at risk – and all at once.
Have you heard of a hack in which your data might have been part of?
Run antivirus software, check your online accounts, and change your passwords immediately. If any account activity is flagged as potentially suspicious, take immediate steps to secure them.
Potential hacks are hiding everywhere. If you want to be safe, you must be aware.
Here is a closer look at recent news of hacks & scams from around the world.
The Facebook Fine

You can read about the Facebook data breach here: Global Tech Roundup: Facebook Faces $3.4Bn Fine for Latest Data Breach (technext.ng)
In one of the largest data breaches to hit social media, Facebook reportedly saw the information of 533 million users accidentally go public during a malicious attack on the online giant.
Information compromised includes details that users had not agreed to make public, such as personal phone numbers and email addresses.
According to reports, hackers had posted the information lists on various message boards for the taking.
While Facebook has claimed that the leaked data was “old”, it has not reassured their users or investors much. A $3.4 billion fine is expected to be paid by the company for its reaction to the hack.
The European Poker Tour

You can read about The European Poker Tour data breach here: https://www.cardschat.com/news/danish-poker-pro-found-guilty-of-running-online-poker-malware-scheme-86110/.
While the name Peter Jepsen might not be familiar to most people, to poker players, he is an international world champion player – and unfortunately, also guilty of a massive malware scandal involving European Poker Tour games.
Jepsen is reported to have installed malware on the systems of competing players. The software gave Jepsen the ability to view opponents’ hidden cards at will – and if you have not guessed, that is bad.
He was caught when his behavior was reported by other players, and an estimated $3.9 million worth of assets were seized.
The Bitcoin Heist

You can read about The Bitcoin Heist data breach here: https://indianexpress.com/article/cities/bangalore/bengaluru-25-year-old-govt-portal-hacker-sent-to-13-day-ccb-custody-7085208/
A 25-year-old hacker from India known by the alias “Sriki” has been caught by the Bengaluru Central Crime Branch after hacking into multiple websites that include cryptocurrency exchanges, government websites, and poker sites.
After hitting one site too many, the hacker was arrested, and approximately $1.2 million in stolen cryptocurrency assets were seized. Additionally, he was hit with an almost two-week custody period.
The Zondo Break-Ins
You can read about The Zondo Break-Ins here: https://www.businesslive.co.za/bd/national/2021-04-18-burglary-at-state-capture-commission-office-treasonous/
Computers that could contain sensitive information were stolen during a burglary at the Zondo commission offices in Johannesburg, South Africa during April 2021.
At the time of writing, the extent of the stolen information has not been reported – but concerns have already been raised, and security levels reportedly increased to stop such an incident from happening again.
It is proof that cybersecurity threats do not just occur on the internet but might very well cross over into what people see as the real world. Protecting your computer’s software is not enough to ensure that a cybersecurity threat will not happen.
Always remember to keep your most important data under lock-and-key. Practical lock or alarm systems for computers exist – and some high-tech ones can alert the authorities if anyone tries to gain access to the system.
Even if your personal information does not seem like national security to you, always guard your data (and the device where it is saved).
The University Networks

Stanford and the University of California reported a serious attack on their user database in April 2021, and immediately cautioned all users to take protective measures on their personal systems.
University systems contain vast amounts of data, including the information of students and teachers. Unfortunately, this means that university servers are too often targeted by penetration attacks.
In this case, information was held up in a ransom-ware attack, with hackers demanding money for files that had been gathered through an exploit in the Accellion file sharing software.
The Domino’s Breach
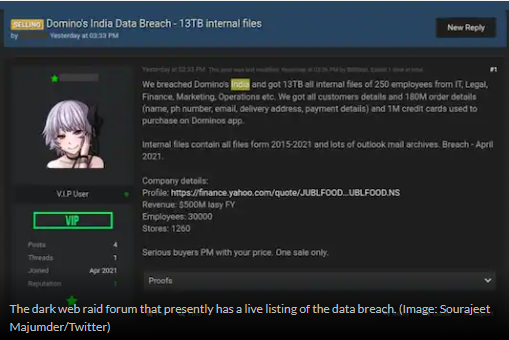
The Domino’s Breach
You can read more about The Domino’s Breach here: https://www.news18.com/news/tech/dominos-india-hack-7-years-of-internal-docs-10-lakh-credit-cards-on-sale-for-rs-3-4-crore-3655799.html.
While a pizza chain seems like one of the most unlikely hacks you will hear about, consider the amount of customer information which your average company hangs on to.
Every order has an address, and every address has a name – and added to this is the possibility of credit card information tied to the rest. Pizza companies also record phone numbers, routes, regular orders, and other information a hacker could potentially hawk online.
ADomino’s server in India saw an incredible 13TB of customer data and company documents sacrificed to a hack.
Does that make you worry about how seriously your local pizza restaurant takes their cybersecurity just yet?
The Ashley Madison Hack

You can read about The Ashley Madison data breach here: https://ewn.co.za/2015/07/20/175000-South-African-cheaters-caught-up-in-Ashley-Madison-saga .
The Ashley Madison exploit was widely reported in 2015, when the niche infidelity-themed dating website was compromised – and with it, the information of an estimated 175, 000 users at once.
It just goes to show that almost any website holding user data could become vulnerable to a cyberattack.
Regardless of what people might think of the Ashley Madison business model, it is a scary take on how easy data can be to compromise.
Are you careful enough about the information you have posted online, or could a hacker retrace your steps straight to your doorstep?
The Life Healthcare Group Breach

You can read about The Life Healthcare Group Breach here: https://ewn.co.za/2020/06/09/life-healthcare-group-hacked-amid-covid-19-fight
Healthcare is a multi-billion-dollar industry, with hospital servers and medical funds holding the user information and medical data of millions.
Doctor’s offices, admissions desks, and accounting departments are just some of the healthcare avenues worth mentioning – and everywhere, user data is entered into a system or server for every consult or correspondence.
What happens when healthcare systems get hacked?
In June 2020, Life Healthcare Group experienced a serious breach of their server which saw data saved on “admissions systems, business processing systems and email servers” compromised.
As a mainstream medical group in charge of private hospitals and doctor’s consulting rooms, the data breach presented an immediate danger.
In an urgent statement, Life Healthcare Group switched all systems over to manual to minimize the potential damage.
Are you still sure that your identity is safe everywhere?
This is a guest post contribution from Alex J Coyne
Editor’s Note
Alex writes excellent cybersecurity guest post articles for us and it looking for paid work in that field. If you are looking for a top cybersecurity writer send us an email at john@identity-theft-scout.com and we will put you in touch with him.
Disclosure:
One of the purposes of publishing this article is to make you aware that if you are working online, whether as employee or freelancer working from home, that you must be aware that you need to have first class cybersecurity software and be using a virtual private network, preferably provided with your cybersecurity software. We use and recommend Bitdefender Total Security software plus their Virtual Private Network. We are also their affiliates in promoting the service.


