Fictional portrayals of computer programming, hacking, and cybersecurity are often exaggerated – and far too often, they come across as totally inaccurate to experts and enthusiasts.
How many times have you watched a hacking scene in a movie or television show, and thought things did not look quite right? Have you ever thought that a video game’s portrayal of cybersecurity is completely off the mark?
It takes more than a few lines of code to test a server, there is rarely a single large red button, and computer users do need the mouse – but that is not what most fictional portrayals would have you think penetration testing or programming really looks like.
More accurate cybersecurity and hacking portrayals in video games exist!
All programmers love the potential that a good puzzle holds. That is why many people with an interest in cybersecurity naturally take well to gaming.
Do you feel like a challenge – but with the benefit of accuracy?
Here are the most accurate video games about cybersecurity & hacking.
System Shock 2
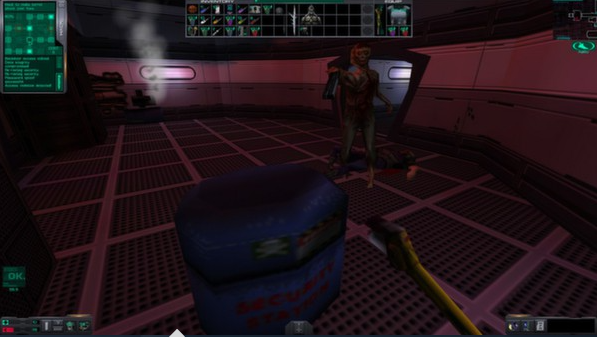
System Shock 2 was first released in 1999 as a futuristic survival-horror first-person shooter with added role-playing aspects.
If you are a fan of any high-octane action games (or creepy survival games), you must play System Shock 2 at least once.
What puts it on this list of great cybersecurity and hacking games is the aspect of augmenting the player or altering the environment. It is more visual than command-line, but it is still accurate (and very, very complimentary to the rest of the game).
Enter the Matrix

Enter the Matrix was released for PC and various console platforms in 2003.
The game takes the player into the Matrix universe, with a third-person shooter perspective throughout most of the gameplay. Combat and the ability to slow time down for fighting sequences (or dodging bullets) added whole new elements that have been widely copied in other games.
Where does the hacking come in?
Players can “hack” into the Matrix through an elaborate command-line interface at any point during gameplay. Easter eggs from the series and upgrades for the player are available when this is done right.
Uplink
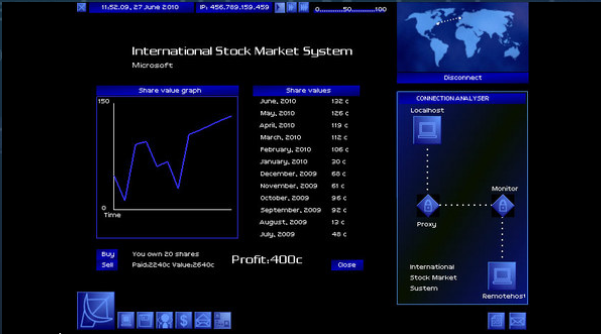
Uplink was released in 2001 and is one of the few games that exclusively functions through a visual user-interface which the player uses to access various game features.
It is a fictional hacking simulation which puts the player into the system of a futuristic, anti-corporation hacker-for-hire. Jobs can be searched for on classified boards, and the player has their choice of which jobs they want to accept.
In-game currency is earned and used to purchase software or system upgrades to improve the ability or speed of your virtual hacks.
Points for accuracy, and the extreme elaborate nature of the game in which the player is free to do as they like to earn their living.
Hacker

Hacker is a classic title released in 1985, when it seems like most of popular culture was still trying to figure out what the word “hacking” means.
It is like Uplink in its anti-establishment storyline, though relied far more on the command-line aspects of hacking to make the game. It plays well, and its complexity has literally stood the test of time.
If you were to play it today, it is still an excellent game – and a better portrayal of command-line programming in fiction than most modernized stories would manage.
Hacker II: The Doomsday Papers
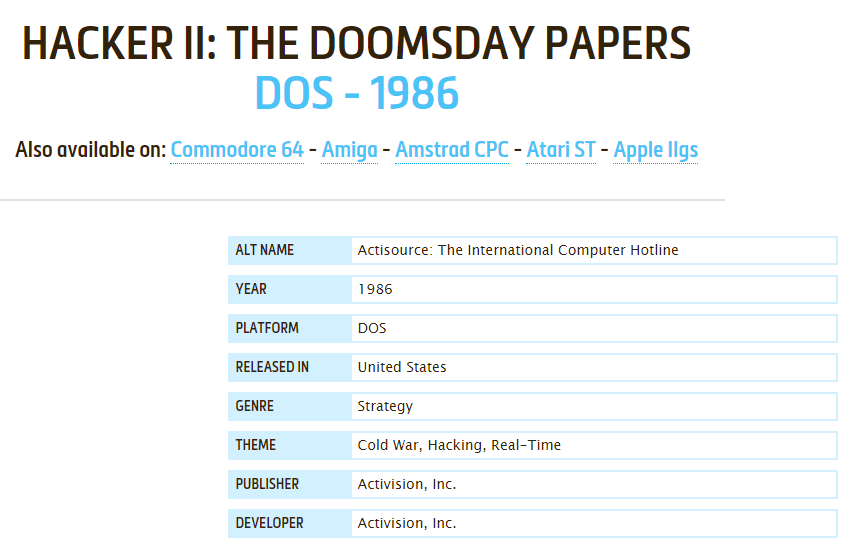
The almost immediate popularity of the first Hacker title spawned a sequel the next year with Hacker II: The Doomsday Papers.
For the most part, the storyline builds on the one laid by the first – and the command-line programming aspect is kept.
Like the first game in the series, it is almost more accurate than many fictional cybersecurity portrayals that you would see today. The good news is that the game is perfectly understandable even if you did not play the first one.
Play it, and you surely will not be disappointed.
Hackmud

Hackmud is a modern mixture of a hacking simulator and an RPG.
The game relies heavily on a command-line interface, with an added cyberpunk theme and storyline that is written well enough to make players forget about “fancier” game visuals. Hackmud is elaborate and meant to be played in real-time.
So far, it is one of the most accurate hacking simulation games out there and has been praised by its accuracy since its release.
Have you tried Hackmud yet?
If not, you should.
Street Hacker
Street Hacker was released in 2004, and almost immediately praised by critics for its accuracy in portraying real cybersecurity threats weaved into a fictional storyline.
Players assume the role of a “street hacker” in much the same style as other hacking games.
Why this game gets mentioned is the accuracy in portraying command-line programming on Linux systems.
In gaming, that is a rare thing for developers to get right.
Street Hacker hits the spot for anyone interested in game development, cybersecurity, or programming.
HEX Hacking Simulator

HEX Hacking Simulator is described well enough by its name.
Created by Solis Studios, it is another game which draws on the hacker-for-hire idea – but this time, the game incorporates malicious cybersecurity terms from real life (like worms versus horses) and explains them in-game.
For accuracy on which cybersecurity nasties do what in practice, this title gets it right.
Students of tech, pay attention.
tryhackme

TryHackMe is partially a game, but partially a real-life server simulation – with a website that encourages penetration testing with programming and exploitation challenges for users.
“Hacktivites” and other challenges like “King of the Hill” let users test their programming and penetration skills in real-time, against real puzzles and programs built for the purpose.
It is a popular idea, with more than 400, 000 users involved in this real-life cybersecurity simulation site.
Could you learn how penetration testing really works?
TryHackMe can teach you.
This is a guest post contribution from Alex J Coyne
Editor’s Note
Alex writes excellent cybersecurity guest post articles for us and is looking for paid work in that field. If you are looking for a top cybersecurity writer, send us an email at john@identity-theft-scout.com and we will put you in touch with him.


