DDOS attack mitigation services matter to businesses. DDOS attacks are a common thing now, and not even a day passes by that you don’t hear about another DDOS attack. Cyber hacking attacks use malicious codes to change the computer code, data, or logic in order to steal or manipulate the data, or to crash a system.
DDOS attacks are different from hacking attacks, but DDOS mitigation services matter for businesses because they can prevent the overwhelming of a website which would otherwise put a business’s website offline to customers.
Since most enterprises and businesses today operate on a technology-dependent network, these breaches can seriously compromise the system and the data security of the entire organization. And not only of that organization but of the people who rely on and use the services of that organization as well.
What is a DDOS attack?

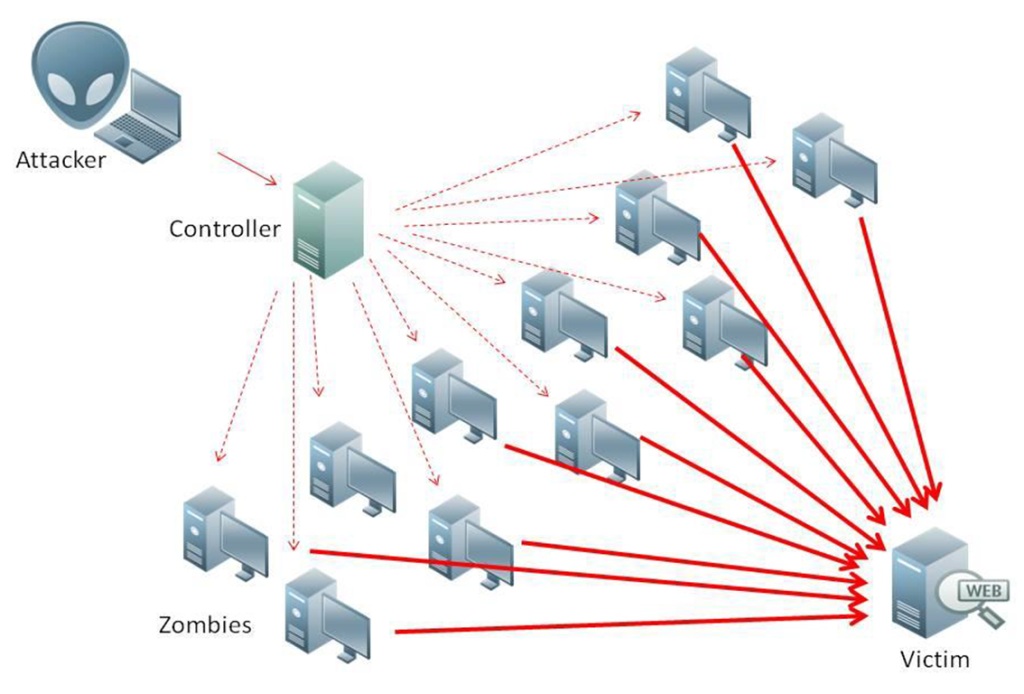
Distributed denial-of-service (DDOS) attacks are one type of cyberattack that render websites and other online services unavailable to its users. DDOS attack is an attack where numerous compromised systems attack one target which in turn causes a so-called ‘denial of service’ for users using that system. The incoming messages from these compromised sources cause the system to basically shut down.
How is DDOS different from a DOS attack?
Before we move on, let’s see how these two differ. In a DOS attack, an attacker uses one internet connection to either take advantage of a computer’s vulnerability or send an overwhelming flow of fake requests so as to cause a server to crash by exhausting its resources.
Distributed denial of service (DDOS) attacks, on the other hand, are carried out from various connected computers. There is usually more than one person involved and since the attacks are coming from more than one device at the same time it is more difficult to dodge the attack. DDOS attacks target the network in an attempt to overwhelm its resources with immense amounts of traffic.
How does a DDOS attack happen?
In this type of attack, a perpetrator can use your malware-infected computer (and many more malware-infected computers) to remotely target another device.
An attacker must first hijack computers by installing malware to remotely control them. This is accomplished by exploiting a target computer’s disadvantages, such as a low-security system or other weaknesses they can find. Then, through these computers, they can send system overwhelming amounts of data to the target website or system overwhelming amounts of spam to a particular email address or addresses.
It is called a ‘distributed’ attack precisely because the attacker is using several computers, including yours, to trigger the DDOS attack.
What are the main types of DDOS attacks?
The Internet has played a leading role in economic rise and prosperity, but everything great comes with a price. One such price is the rise of DDOS attacks, which stands for Distributed Denial of Service. DDOS attacks have evolved over the years and today there are various types of DDOS attacks.
There are many different acronyms and terms which can sometimes be confusing. But that’s why we are here to clear the mystery for you.
Let’s take a look at the most common and most dangerous types of DDOS attacks:
UDP Flood
A User Data Protocol Flood (UDP) attack floods the ports on the target device with IP packets that contain UDP datagram – which is a connectionless networking protocol. By flooding the random ports on a remote host, this type of attack is making the host device to listen for applications on those ports and respond with an ICMP packet. This eventually dries out the sources and renders the system inaccessible to its users.
SYN Flood
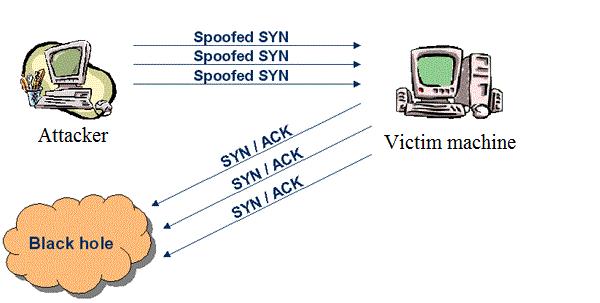
This type of DDOS attack focuses on the “three-way handshake” – a defect in the TCP connection sequence. Syn Flood – aka TCP SYN, uses this weakness to exploit all the resources of the target server, therefore, making it unavailable. What basically happens here is that perpetrator sends TCP requests extremely fast and the target device can’t process them which causes the crash in the system.
Ping of Death
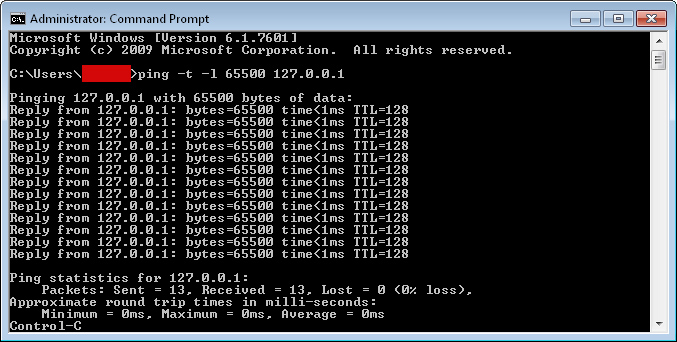
Ping of Death attack or POD happens when the offender sends malicious or oversized pings to crash or freeze the target device. The maximum length of the IP packet is 65,535 bytes. However, there are limits to maximum sizes per each frame, so a larger IP packet always has to split between many IP fragments. But when POD strikes, since the fragments are malicious and oversized, the target machine ends up with a packet bigger than 65,535 bytes which in turn causes the device to freeze or stop working.
Slowloris
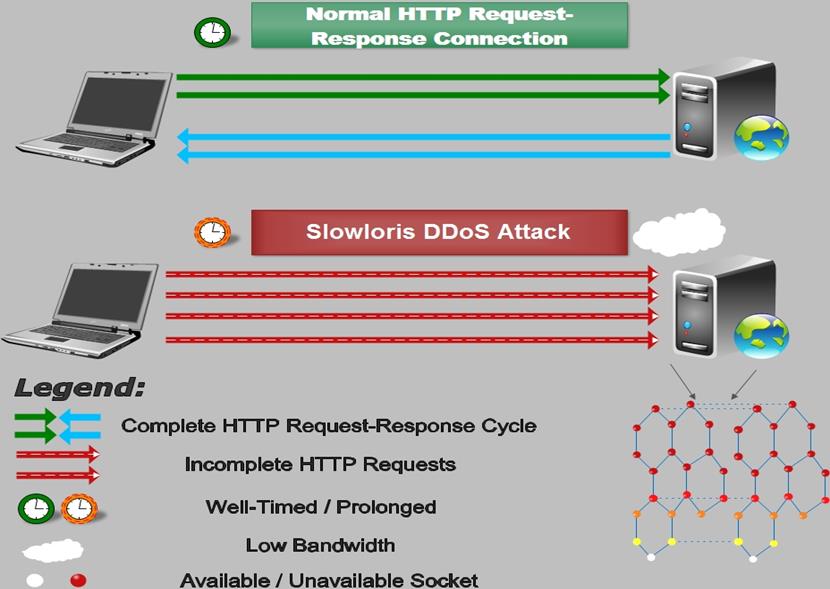
Slowloris attack is a powerful DDOS attack where a single device can take down a whole web server. This type of attack is simple yet extremely effective as it requires minimal bandwidth to target the web server, without harming other services and ports. As the name itself indicates, Slowloris is slow but steady. Slowloris is known to be used by many ‘hacktivists’ to attack government websites.
NTP Amplification
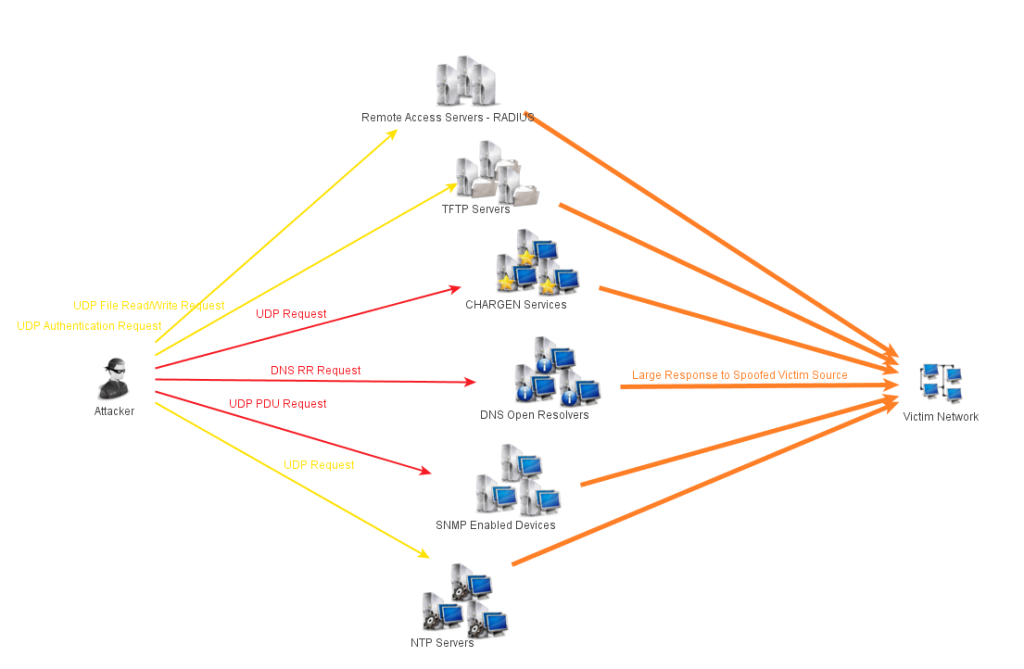
NTP Amplification attack is basically a type of reflection attack – only amplified. In this type of attack, attackers elicit a response from the server from a fake IP address. The attacker uses the publicly accessible Network Time Protocol (NTP) servers to attack and overwhelm the target UDP (User Datagram Protocol) traffic.
Watch this video to learn more about DDoS Attack mitigation
Sign up today and try Incapsula’s Business Plan Free for 7 days.
Conclusions
Mitigating Distributed Denial of Service (DDoS) attacks requires a combination of proactive measures and reactive responses. By implementing solutions such as increasing network capacity, rate limiting, traffic filtering, and utilizing content delivery networks, organizations can enhance their defenses against DDoS attacks.
Additionally, leveraging DDoS mitigation services, load balancing techniques, intrusion detection systems, and network segmentation can help detect and mitigate attacks more effectively. Regular system updates and patches, along with the development of an incident response plan, are crucial for maintaining a robust defense against DDoS attacks.
Remember that DDoS mitigation is an ongoing process that requires continuous monitoring and adaptation to emerging threats.


